Hardware Security Module – The Whitepaper
Safety first. Hardware security modules play their essential part in storing cryptographic ciphers, protecting them from unauthorized access, and allowing the keys to be used by authorized applications without allowing the keys to be extracted.
You can read our contribution to hardware security in this article on Hardware Based Security - a recommended read that takes about seven minutes of reading time and - believe us - is worth every minute of it.
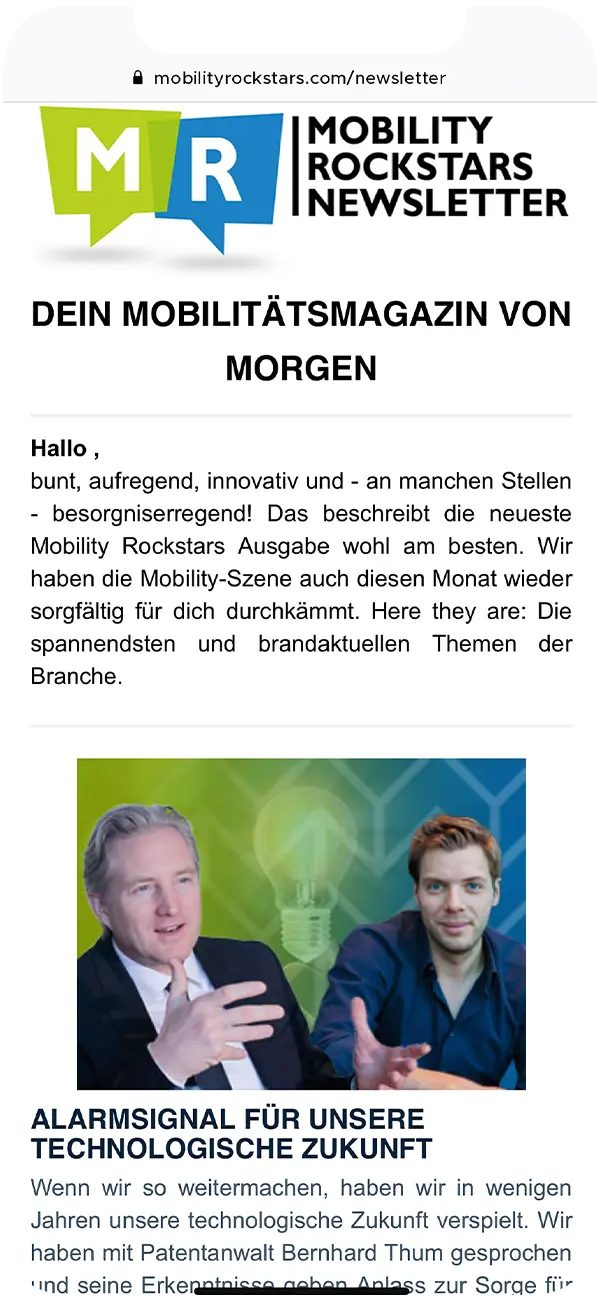
However, here and now we are talking about hardware security modules, the most common errors in their use and, of course, how to fix or avoid these errors.

Marc
Marketing Professional
11.01.22
Ca. 3 min
Hardware Security Module – Read or download free whitepaper
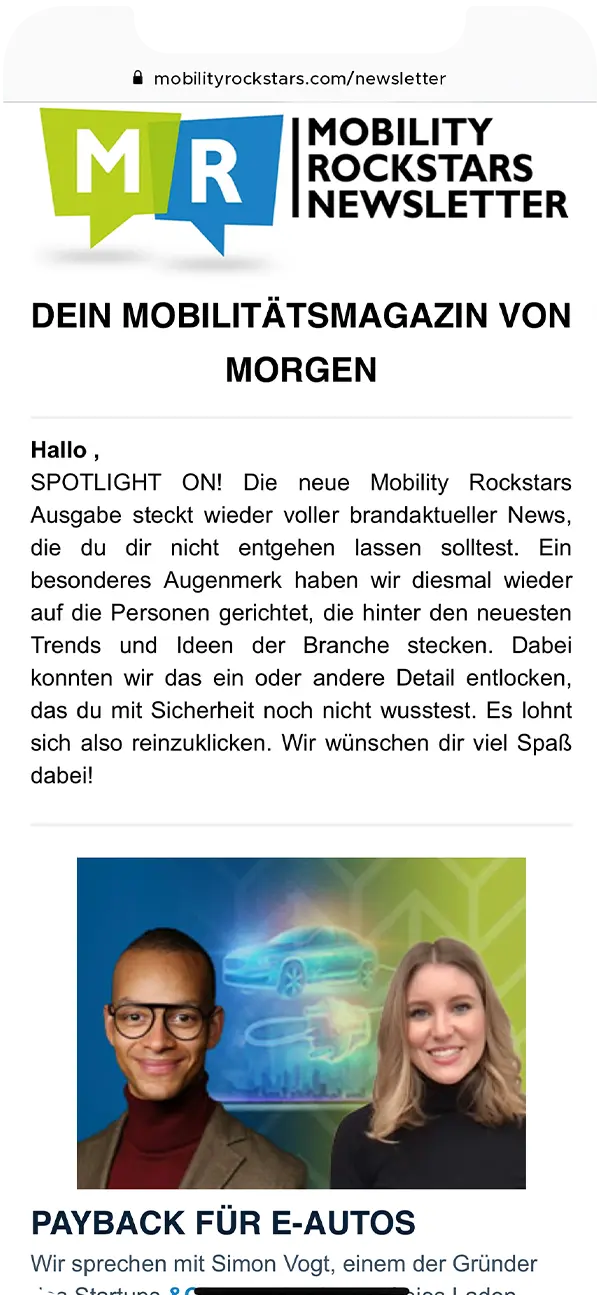
The Cloud IT team of Cognizant Mobility, including the author of the whitepaper Eduard Pop, offers you today this international and therefore in English whitepaper on the topic of error insight and prevention in hardware security modules.
We address problems such as the vulnerability of interfaces or different implementation standards as well as explanations of a versatile, future-oriented approach to this highly sensitive security topic. We hope you enjoy reading and would be happy to welcome you on our LinkedIn company account of Cognizant Mobility as well. Alternatively, we recommend our newsletter, which is of course also free of charge, in which we always shed light on the major topics of cloud IT, data science, testing and UWB technology in an informative, often exciting and sometimes quite entertaining way.
But now we wish you a lot of fun with the Hardware Security Module Whitepaper: